Cryptocurrency Wallets Explained

A software application known as a cryptocurrency wallet is responsible for safely storing both your public and private keys. Your digital wallet relies on these key pairs, also known as secure digital codes, in order to interact with a blockchain and provide you with the ability to check your balance, transfer and receive cryptocurrency, and more. You might think of your wallet as similar to a local bank branch or an ATM that gives you access to your money that are housed inside the bank, or blockchain, in the case of cryptocurrencies.
Keep in mind that the blockchain is a publicly accessible and very secure ledger that records and verifies all cryptocurrency transactions. Because cryptocurrency currencies are digital rather than tangible, anybody who is just getting started in this space should bear in mind that cryptocurrency wallets do not hold any actual coins.
Another illustration is provided below in the hope that it clarifies the previous one. This time, let’s compare a cryptocurrency wallet to something that you most likely make use of on a regular basis, which is your email.
Your cryptocurrency wallet functions very similarly to an email account; however, although you do provide your email address, you do not disclose your password. You may think of your public keys as being analogous to your email address, and your private keys as being analogous to the password that you use to log in to your email account. You do something very similar to providing your email address to your contacts so that they can send you messages by having them provide you your wallet address so that they can pay you money.
If you are concerned about maintaining the security of your email account, you should under never circumstances reveal the password to anybody. In a similar vein, if you want to ensure the security of the coins stored in your cryptocurrency wallet, you should never reveal the private keys (or the password or passphrase) to your cryptocurrency wallet.
How do cryptocurrency wallets work?
Your cryptocurrency wallet acts as a connection between you and the world of digital money, more specifically blockchains. It grants you access to your digital money and enables you to engage with the ledger that keeps track of all crypto transactions.
All types of cryptocurrency wallets, including Bitcoin wallets, Ethereum wallets, and standard wallets, operate according to the same fundamental principles utilizing a set of tools known as keys. However, in the same way that these are not actual wallets that you transport about with you, neither of these are actual keys that you transport around with you.
Every technique for storing digital information consists of three components: a public address, a public key, and a private key. These are the actual keys to the kingdom when it comes to keeping your Bitcoin safe and conducting transactions online.
What is a public address?
A public address is an identification for your cryptocurrency wallet that is viewable by the public. It is the target destination for digital currency of which you buy ownership. When you make a purchase of cryptocurrency, the seller will transmit a record of ownership to the public address you provide during the transaction. In most cases, you will be required to submit your public address in order to complete a transaction. This is analogous to how you would supply your BSB and bank account data in order to complete a conventional money transfer via a bank.
What is a public key?
There are some similarities between a public key and a public address, but they are not the same thing. It validates the fact that you are the owner of a public address that is capable of sending and receiving cryptocurrency.
A public key is a collection of letters and numbers that is generated at random.
An example of a public key could be: 0x286717D6E417A7801d0ecED32d8b7Ff2241078d6.
Public keys are matched to the private key held within the crypto wallet but unlike traditional banking details, these keys do not provide any information about the wallet’s owner.
What is a private key?
When it comes to cryptocurrency wallets, a private key may be thought of as a form of password. It is inward-facing and allows users to access their crypto wallet to buy, sell, and monitor their digital currency. Consider it the same way you would consider the password to your email account. It is the central cog in the security system for your coin.
What types of crypto wallets are available?
There is a plethora of choice when it comes to wallets for cryptocurrencies. The one that is ideal for you will depend on the nature of your typical transactions as well as the one that gives you the most sense of security given the circumstances.
There are primarily two kind of wallets: hot storage wallets (also known as digital wallets), and cold storage wallets, also known as hardware wallets (physical). When it comes to determining which cryptocurrency wallet is ideal for you, there is not always a right or wrong answer since both hardware and software wallets have their own advantages and disadvantages.
Protecting your cryptocurrency holdings has never been more crucial given the ongoing rise of the cryptocurrency sector. High-profile hacks are still a problem twelve years after the creation of the world’s largest digital asset, with hostile actors able to flee into the night with millions of dollars in ill-gotten profits. Many centralized exchanges, thank goodness, now have insurance plans to safeguard against such occurrences, and they also put away a portion of their revenues in case they need to compensate their consumers.
What Is Hot Storage?
Hot storage is used to describe crypto wallets that are connected to the internet. These wallets can operate on a variety of devices, including mobile phones, tablets, and desktops, and they are perfect for maintaining a limited quantity of digital assets in a safe environment.
Even though they are extremely mobile and give you the ability to access your digital assets anywhere, funds held in hot storage can be vulnerable if malicious actors are successful in hacking into the device where a wallet is stored. This is the case even though hot storage wallets give you the ability to access your digital assets anywhere.
What Is Cold Storage?
Cold storage, on the other hand, does not have any kind of connection to the internet, in contrast to hot storage.
The majority of the time, a cold wallet will take the shape of a physical item, such as a piece of hardware that is both diminutive and condensed in size.
Do you favor writing down your public and private keys on a sheet of paper (while using extreme caution)? Congratulations! This is another kind of cold storage that may be used. (Even while this does remove the possibility that a hacker would be able to acquire a private key, it does introduce a new risk: that you may misplace the piece of paper, in which case you will no longer have access to your cryptocurrency.) Because of this, it’s very uncommon for individuals to keep such kinds of paper in safes and vaults — basically anyplace that’s lovely and secure — with extreme caution and attention to detail.
When they are not being used, bitcoin wallets are considered to be cold storage if they are not linked to the internet or any other unsecured networks. This is done in order to give an extra layer of protection on top of that which is supplied by the more prevalent hot wallets. Hot wallets are software wallets that are either saved on a user’s local computer or accessible from the servers of a service provider through a website interface.
Cold wallets are used by individual cryptocurrency users as an affordable and relatively simple method of insulating one’s crypto funds against the threat of hacks, phishing, and other vectors of attack that may lead to the permanent loss of coins. Users of cryptocurrencies like Bitcoin and Ethereum use cold wallets.
They are in even higher demand with firms that maintain custody over the cash of their clients, such as bitcoin exchanges, due to the fact that these types of enterprises are more common. By holding the currencies that belong to tens or even hundreds of thousands of users in a centralized manner, these firms become particularly appealing targets for hackers. The only guaranteed approach to safeguard against assaults is to physically separate the majority of the reserves from the Internet.
Cold Storage Comes In Many Different Forms, The Two Most Popular Ones Being Paper And Hardware Wallets.
A sheet of paper on which the public address of the wallet as well as the private key of the wallet have been written constitutes a “paper wallet.” The public address is required in order to receive bitcoin, whereas the private key is necessary in order to retrieve previously saved cash and to transfer cryptocurrency. For convenience’s sake, paper wallets often come equipped with QR codes that can be scanned using a smartphone camera.
An electronic device known as a hardware wallet is one that cannot be accessed without first being physically connected to a computer. These may vary from amateur, handmade innovations to consumer devices that are available for purchase commercially (typically in the form-factor of a USB stick or drive), all the way up to proprietary solutions created by professional engineers specifically for a client’s needs.
Most widespead examples of this being the Ledger Nano and the Trezor.
Ledger manufactures cold storage wallets designed for users who want increased security. Their wallets are a physical device that connects to your computer. Only when the device is connected can you send Bitcoins from it. Ledger offers a variety of products, such as the Ledger Nano S and the Ledger Nano X (a bluetooth connected hardware wallet).
Trezor is a pioneering hardware wallet company. The combination of world-class security with an intuitive interface and compatibility with other desktop wallets, makes it ideal for beginners and experts alike. The company has gained a lot of the Bitcoin community’s respect over the years. Trezor offers two main models – The Trezor One and Trezor Model T (which has a built in touch screen).
Other, less popular cold wallet types include smart cards and even sound wallets, which store private keys in the form of audio on CDs or vinyl records.
Hot Storage vs Cold Storage: The Pros and Cons
Both hot wallets and cold wallets come with their own unique set of benefits and drawbacks, just as everything else does.
If we are going to be competitive about it, hot wallets have the advantage due to the fact that they are incredibly simple to use. Because they are already linked to the internet, this is an easy method for gaining access to cryptocurrency. It is not uncommon for them to be free to use, and it is not difficult to locate a wallet that is suitable for usage with any cryptocurrency. Cold wallets, on the other hand, are small enough to fit in your pocket and can connect to your computer via a USB port so that you can do tasks like update the wallet’s software. (On the other hand, there are many who believe that this entails that these gadgets will at some point establish connections to the internet.)
However, much higher levels of protection are the primary rationale for the growing popularity of cold wallets.
To put it simply, hot wallets are particularly susceptible to being hacked. Hackers have been resorting to more complex methods in order to target victims, despite the fact that the majority of providers have solid safeguards in place to give additional protection. In certain instances, fraudsters have established firms that give the impression that they are real in order to acquire someone’s trust and access to their computer.
The primary difficulty associated with cold wallets may be broken down into two parts. First, you’ll need to shell out some cash to get one, which typically costs between $60 and $170, and then you may want some level of technical expertise in order to have it installed properly.
Accounts held on cryptocurrency exchanges may be regarded as “hot wallets,” however the level of protection offered varies significantly across platforms. Exchanges that are more well-known and established often have more stringent security measures in place and hold the overwhelming majority of assets under management in cold wallets. They only maintain a small proportion of assets in hot storage so that users may more easily access their assets.
Famous Hacks Involving Hot Wallets
It should come as no surprise that hot wallets have been the target of a number of noteworthy hacks, given that using a hot wallet is riskier than using a cold wallet to store cryptocurrency.
In September of 2020, KuCoin was the target of a significant hacking assault, during which cybercriminals made off with money from the exchange’s Bitcoin, Ether, and ERC-20 hot wallets. At first, it was believed that just $150 million had been taken, but later on, it became clear that the actual amount taken was closer to $280 million. Thankfully, because to “on-chain tracking,” “contract upgrades,” and “judicial recovery,” at least 84% of these monies were able to be recovered at a later time.
The cryptocurrency exchange Bitpoint, which is owned by the Japanese company Remixpoint, also had its hot wallet hacked in July of this year. The amount of damage was estimated to be 32 million dollars, which is equivalent to about one fifth of the assets that were being managed by the platform. Several cryptocurrencies, including Litecoin, Ether, Bitcoin, and Ripple, were among the assets that were seized. It’s instructive to note that the company’s cold wallets were untouched by whatever happened. However, even cold wallets run the risk of being hacked in certain circumstances, but not in the same manner as hot wallets are susceptible to attack. Ledger, a supplier of cold wallets, was the victim of a breach in December 2020; however, user assets were not taken; rather, customer information was stolen. Over 272,000 customers of Ledger had their names, mailing addresses, and phone numbers leaked online by hackers, making them susceptible to phishing attacks and other deceptive strategies to gain access to their cold storage cryptocurrency. Ledger has apologized to its customers and is working to restore their privacy.
The Ledger event demonstrated that holders of cryptocurrencies should constantly be on their alert and adopt best practices for the secure storage of cryptocurrencies. While this particular “hack” of a cold wallet is rather uncommon, it nonetheless occurred.
How do I decide which wallet to use?
Deciding which type of wallet to use depends on a variety of factors, including:
- How often you trade. In general, hot wallets are better for more active cryptocurrency traders. Quick login ability means you are only a few clicks and taps away from buying and selling crypto. Cold wallets are better suited for those looking to make less frequent trades.
- What you want to trade. As mentioned earlier, not all wallets support all types of cryptocurrencies. However, some of the best crypto wallets have the power to trade hundreds of different currencies, providing more of a one-size-fits-all experience.
- Your peace of mind. For those worried about hacking, having a physical cold wallet stored in a safe deposit box at the bank or somewhere at home, provides the safest, most secure option. Others might be confident in their ability to keep their hot wallets secure.
- How much it costs. It is important to investigate the costs associated with each wallet. Many hot wallets will be free to set up, but charge a fee each time you trade. Meanwhile, cold wallets, like any piece of hardware, will cost money to purchase.
- What it can do. While the basics of each cryptocurrency wallet are the same, additional features can help set them apart. This is especially true of hot wallets, many of which come with advanced reporting features, insights into the crypto market, the ability to convert cryptocurrencies and more. Security features can also be a good differentiator.
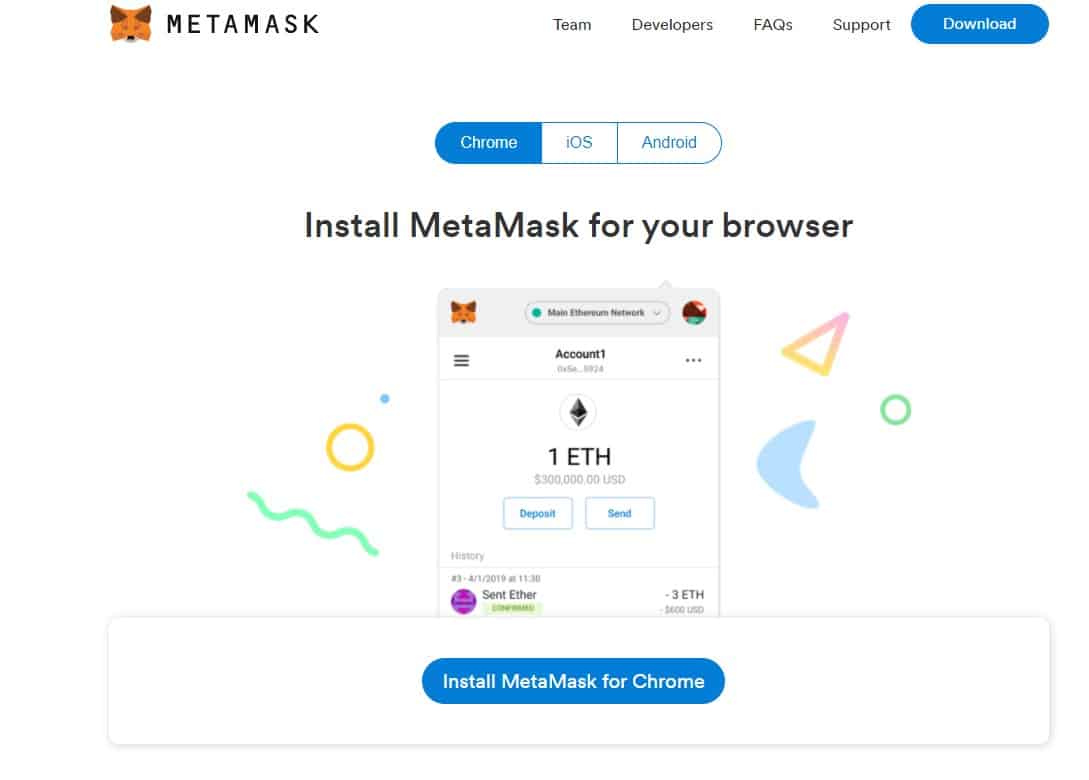
How do I set up a Metamask wallet?
A Quick Recap
Making an investment in cold storage might be beneficial for you if you want to trade bigger amounts of cryptocurrency in the future. It is essential that you do your own study and weigh the benefits and drawbacks of a variety of items available on the market before moving further.
Another important piece of advice is to do a significant amount of research about the safety protocols that are followed by cryptocurrency exchanges. You shouldn’t be surprised if the majority of the assets these platforms are managing are held in a secure location, since this is the standard practice for these platforms.